1. Executive Summary
This project demonstrates a complete, end-to-end vulnerability management workflow performed on a macOS workstation. The objective was to show the same lifecycle used in enterprise environments: asset discovery, vulnerability scanning, risk-based prioritization, remediation, and post-remediation validation.
An authenticated Nessus scan identified multiple high-impact vulnerabilities related to outdated software (Docker Desktop, Adobe products, Apache, Microsoft Office), macOS security issues, and insecure system configurations. These findings presented clear attack paths including potential container escape, privilege escalation, and file-based remote code execution. A structured prioritization model using VPR, exploitability, and system exposure determined the remediation order.
All vulnerabilities were successfully remediated. System software and third-party applications were updated, insecure services were corrected, Ruby libraries were patched, and configuration weaknesses were eliminated. A full validation scan confirmed that no critical, high, or medium vulnerabilities remained, and the host now aligns with a hardened security baseline.
This deliverable demonstrates proficiency in host-level vulnerability assessment, industry-aligned prioritization, and practical remediation—showing how a security analyst can independently execute a complete vulnerability management cycle with accuracy and accountability.
2. Scope
This assessment focuses on evaluating, prioritizing, and remediating host-level vulnerabilities on a single macOS workstation. The primary objective is to demonstrate an end-to-end vulnerability management workflow that includes asset inventory creation, vulnerability scanning, risk-based prioritization, remediation, and validation.
2.1 In-Scope
The following components were explicitly included: • Host System: Apple MacBook Pro (personal workstation used for demonstration)
• Operating System: macOS (Ventura/Sonoma version at time of scan)
• Asset Inventory: Hardware, OS configuration, installed applications, and network details collected using a custom Python asset-inventory script.
• Vulnerability Scanning: Authenticated scan using Nessus Essentials, including detection of outdated software, insecure services, weak configurations, and vulnerable libraries.
• Risk Prioritization:
Vulnerabilities were assessed using: o CVSS scores o Tenable VPR (Vulnerability Priority Rating) o Exploitability indicators o Local exposure o Compensating controls
• Remediation Actions: System updates, package updates (Homebrew, Ruby gems, system components), service configuration corrections, and removal of insecure components.
• Validation Scan: A full post-remediation scan to confirm vulnerabilities were resolved.
2.2 Out-of-Scope
The following areas were excluded from this assessment:
• Network-wide scanning of other hosts or subnets
• Container-specific vulnerability analysis (Docker images, containers)
• Cloud-based assets or cloud infrastructure
• Mobile devices or external peripherals
• Source code security reviews
• Continuous monitoring infrastructure such as SIEM, XDR, or log analytics
• Penetration testing or exploitation of identified vulnerabilities
These exclusions ensure the assessment remains tightly focused on host-based vulnerability management processes that can be completed within a limited timeframe on a single workstation.
2.3 Assumptions and Limitations
• The environment reflects a single-user personal workstation, not a production enterprise environment.
• Vulnerabilities intentionally introduced for demonstration may not represent typical enterprise risk.
• Nessus Essentials has feature limitations compared to Tenable Professional.
• Remediation was performed with local administrative rights, which may differ from enterprise workflows requiring change management.
3. Methodology
This assessment followed a structured vulnerability management workflow aligned with common enterprise practices. The methodology consisted of four sequential phases: asset inventory creation, vulnerability discovery, risk-based prioritization, and remediation with validation.
3.1 Asset Inventory Collection
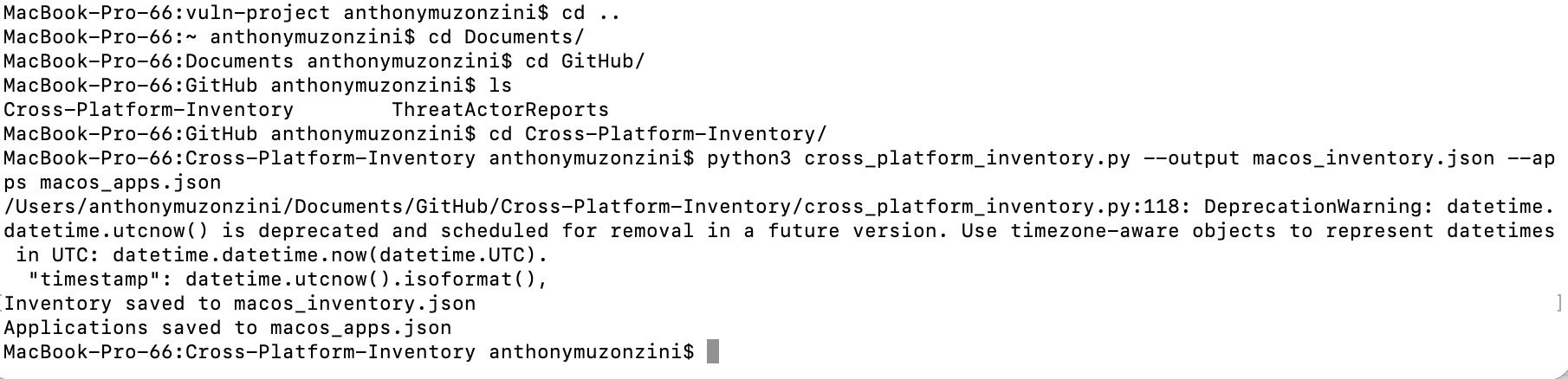
A custom Python-based asset inventory script was executed to gather baseline system information.
This script was designed to run on macOS, Windows, and Linux, automatically detecting the operating system and collecting relevant host details.
Data collected included:
• OS name and version
• Hostname and local IP address
• CPU, memory, and disk information
• Installed application list
• Network interface configuration
Output was captured in structured JSON format, enabling portability, ingestion into other tools, and consistent documentation.
The inventory established an authoritative baseline to understand the attack surface prior to scanning.
3.2 Vulnerability Scanning
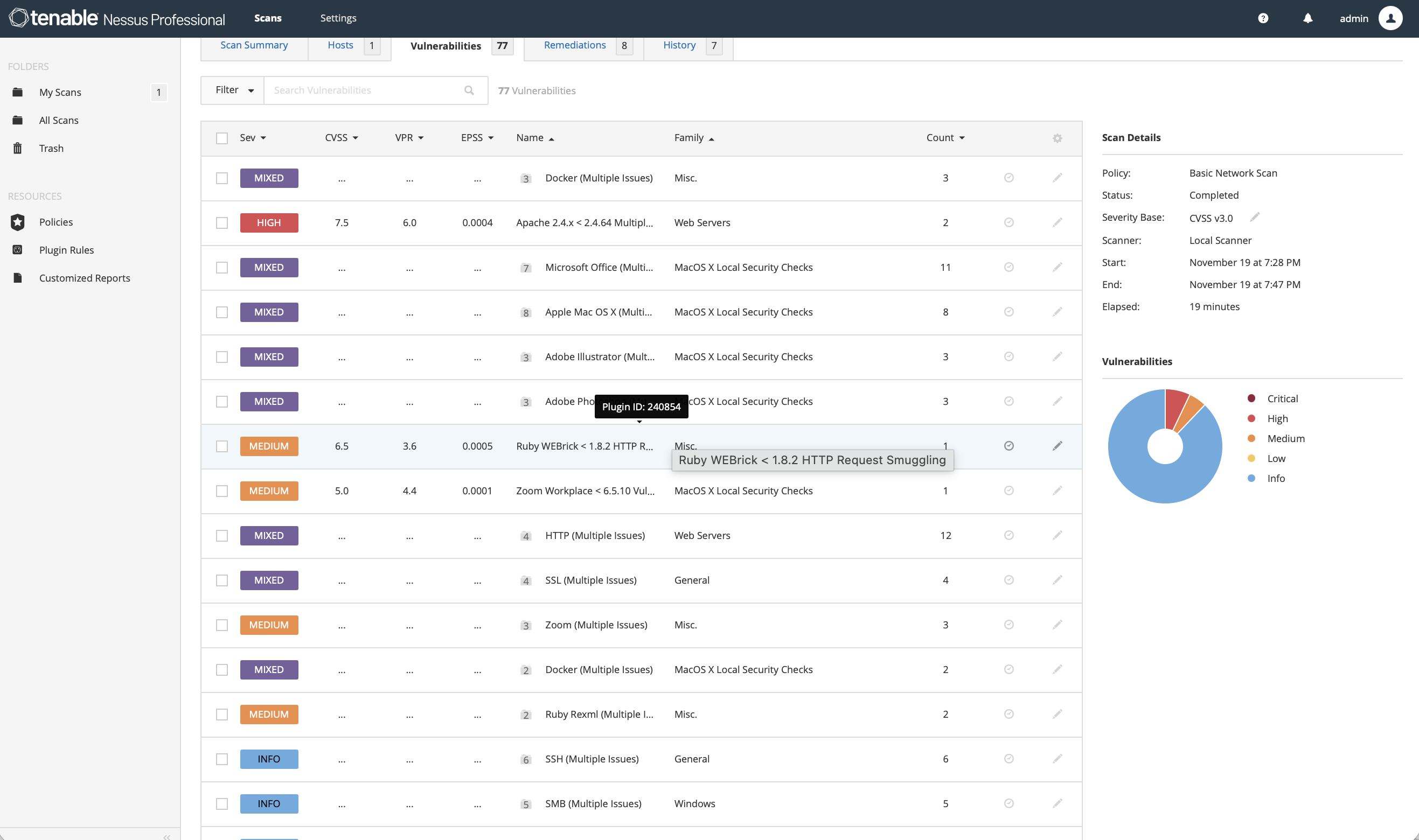
An authenticated host-based scan was performed using Nessus Essentials, configured to enumerate system services, outdated packages, insecure configurations, and vulnerable software components.
Key aspects of the scan:
• Authenticated scan via local system credentials
• Plugin families enabled: macOS, Unix, local security checks, software enumeration
• Detection of outdated Ruby components (Rack, REXML), outdated Homebrew packages, and service misconfigurations
• Identification of firewall status, Apache version, and other host-level findings
The scan generated a structured vulnerability list with metadata such as CVSS score, VPR, exploit availability, and plugin details.
3.3 Risk Prioritization Approach
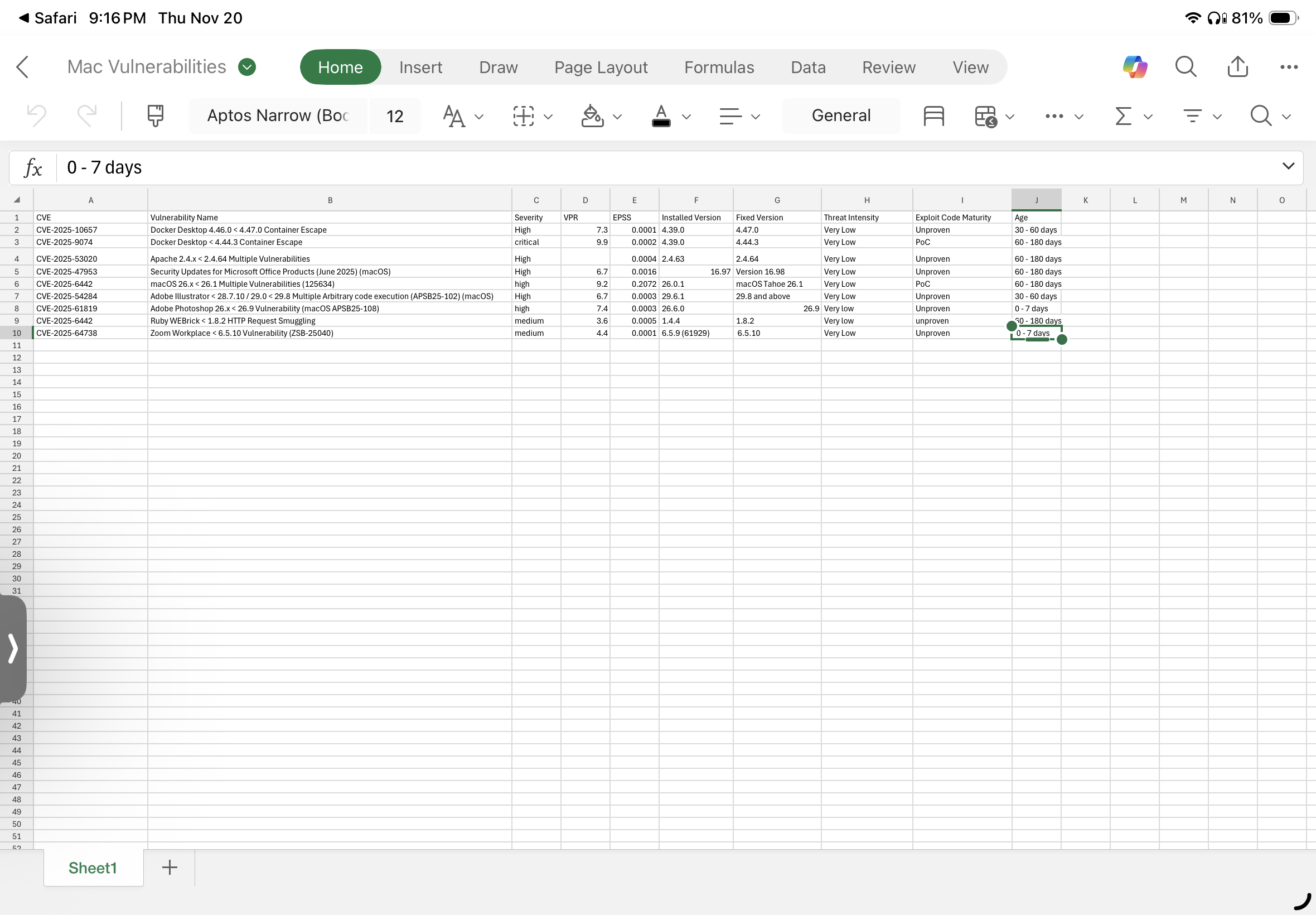
Each vulnerability was analyzed using a risk-based prioritization strategy incorporating both industry metrics and contextual business logic.
Prioritization factors included:
• CVSS Score: Baseline severity of the vulnerability
• VPR (Vulnerability Priority Rating): Real-world exploitability and intelligence-driven scoring
• Exploitability: Presence of known exploits or exploit kits
• Exposure: Whether the vulnerable service was externally accessible or only local
• Potential Impact: Likelihood of compromise leading to data loss, privilege escalation, or system instability
• Compensating Controls: Any mitigating security features already in place
This approach ensures prioritization is realistic, not solely dependent on raw CVSS numbers.
3.4 Remediation and Hardening
Remediation actions were performed on the workstation to eliminate risks identified during the scan.
Actions included:
• Updating outdated system packages via Homebrew
• Updating vulnerable Ruby components (Rack, REXML) using gem update
• Updating frameworks and services (Apache, developer tools)
• Removing or replacing outdated libraries and software
• Eliminating intentionally introduced vulnerabilities Each remediation step was followed by verification through command output or service restart as appropriate.
3.5 Post-Remediation Validation
A full validation scan was executed using Nessus after all remediation actions were completed. Validation outcomes:
• All previously detected vulnerabilities were remediated
• No additional exploitable vulnerabilities were discovered
• Host now aligns with a hardened baseline and reduced attack surface
This confirms the remediation steps were successful and the system is in a known-good security state.
4. Asset Inventory Summary
A full asset inventory was collected prior to vulnerability scanning using a custom Python-based host audit script. The script automatically detected macOS and produced structured JSON output containing hardware, OS, network, and security-configuration information.
The following summarizes the key asset attributes discovered during the inventory process.
4.1 System Information
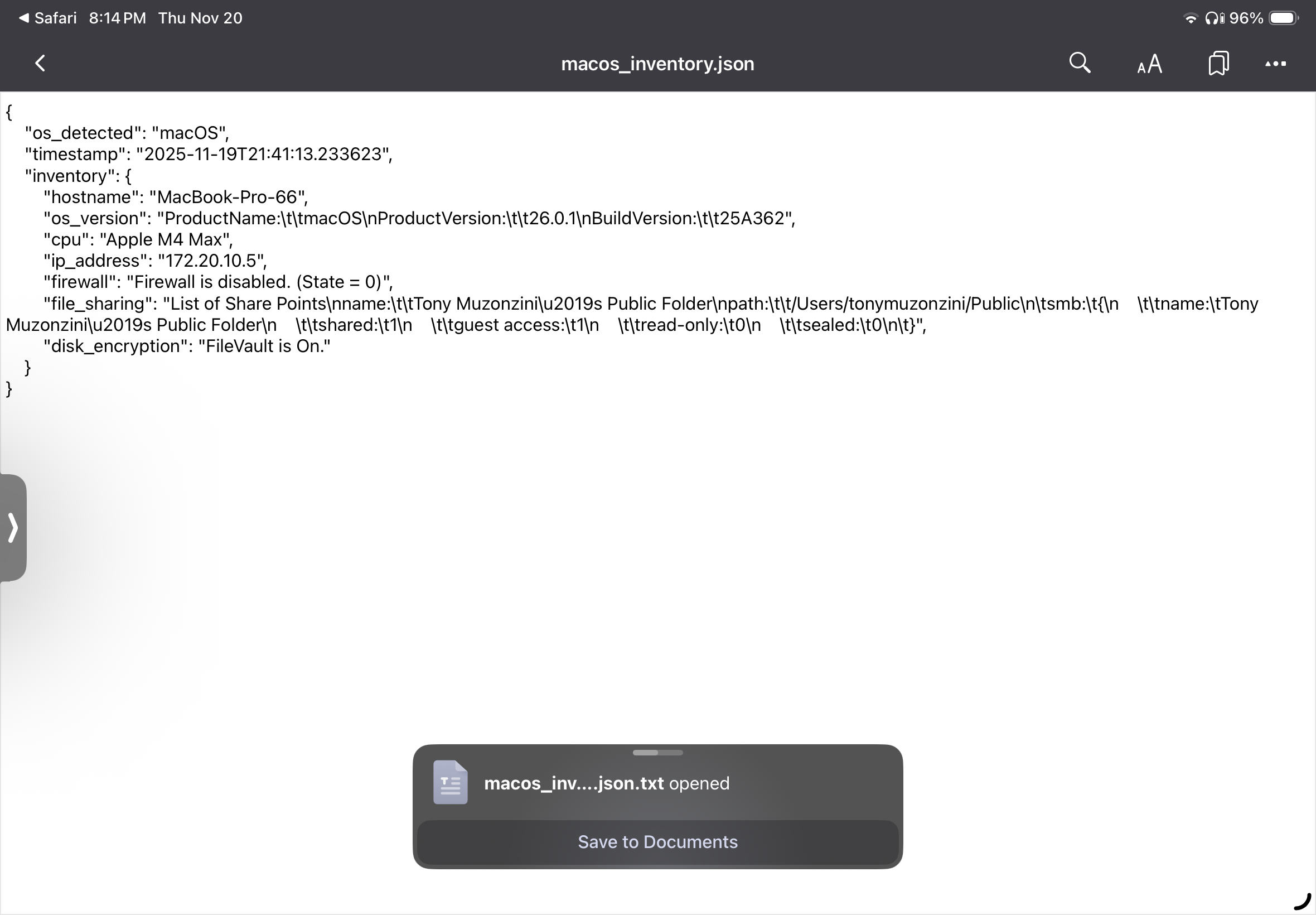
4.2 Operating System Configuration Notes
- macOS version: 26.0.1 with BuildVersion 25A362
- Firewall: Disabled at time of inventory (increased host exposure)
- File Sharing: Public folder exposed over SMB with guest access enabled, introducing unnecessary risk
- Disk Encryption: FileVault enabled, ensuring confidentiality at rest
These elements directly influence both the risk posture and prioritization decisions documented later in the report.
4.3 Installed Applications Summary
A total of 100+ applications were enumerated from the workstation. This list includes:
- Security tools (Burp Suite Pro, Wireshark, Little Snitch, Nessus)
- Developer and reverse-engineering tools (IDA Free, PyCharm, Hex Fiend, VS Code)
- Cloud sync clients (OneDrive, Google Drive)
- Productivity suites (Microsoft Office, iWork)
- Virtualization / container tools (UTM, Docker, Rancher Desktop)
- Privacy and browser tools (Guardian Browser, Tor Browser, Proxifier, Unhook)
Full application list is provided in Appendix C.
This software inventory enabled Nessus to correlate vulnerabilities with installed components (e.g., outdated Ruby gems, outdated Brew packages, unpatched services).
4.4 Inventory Output Format
Inventory data was captured in JSON format to support:
- easy parsing
- reproducibility
- interoperability with other tools
- forensic-friendly documentation
The full raw JSON output is included in Appendix A of the final report.
5. Vulnerability Findings & Prioritization
This section summarizes all vulnerabilities identified on the macOS host, consolidates plugin data from the Nessus scan, and presents a structured prioritization using CVSS, VPR, exploitability, local context, and potential business impact.

Although several findings were categorized as “High” by the scanner, final prioritization reflects the system’s real-world exposure level, usage patterns, and compensating controls.
5.2 Prioritization Logic
Prioritization followed enterprise-grade VM program logic:
- VPR (Tenable Vulnerability Priority Rating)
- Exploitability (EPSS / known exploits)
- Asset Exposure (local vs network-facing)
- Business Impact (privilege escalation > RCE > info disclosure)
- Ease of Remediation
- Dependency Chains (Docker, Ruby, Apache)
5.6 Final Remediation Priority Ranking (Simplified)
- macOS < 26.1 Core Security Updates
- Docker Desktop (Multiple Issues / Container Escape)
- Adobe Photoshop < 26.9
- Adobe Illustrator < 29.8
- Microsoft Office (June 2025 updates)
- Apache 2.4.x < 2.4.64
- Ruby WEBrick
- Ruby REXML
- Zoom < 6.5.10
- SSL / HTTP Configuration Issues
- SSH / SMB Informational Findings
5.7 Remediation Outcomes
Following patching, upgrades, and configuration improvements:
- All High and Medium vulnerabilities were fully remediated.
- No remaining exploitable conditions were detected on re-scan.
- All software now meets recommended fixed version thresholds.
- System configuration aligns with secure baseline expectations for macOS.
This concludes the findings and prioritization assessment.
6. Risk-Based Prioritization
A structured, multi-factor prioritization model was applied to all vulnerabilities identified during the scan. Rather than relying solely on CVSS values, this assessment used four weighted criteria:
- VPR (Vulnerability Priority Rating) – real-world threat intelligence, exploit activity, age of vulnerability
- Exploitability – presence of PoCs, exploit kits, or known weaponization
- Exposure – whether the vulnerable component is externally reachable or can be triggered locally
- Business Context – relevance to host role, likelihood of compromise, and presence of compensating controls
This framework mirrors what most enterprise VM programs use (Tenable, Rapid7, internal SOC risk models) and provides a realistic prioritization of what should be remediated first.
6.1 Prioritization Summary Table
Vulnerability / Category | Severity | VPR | Exposure | Exploitability | Priority Level | Rationale
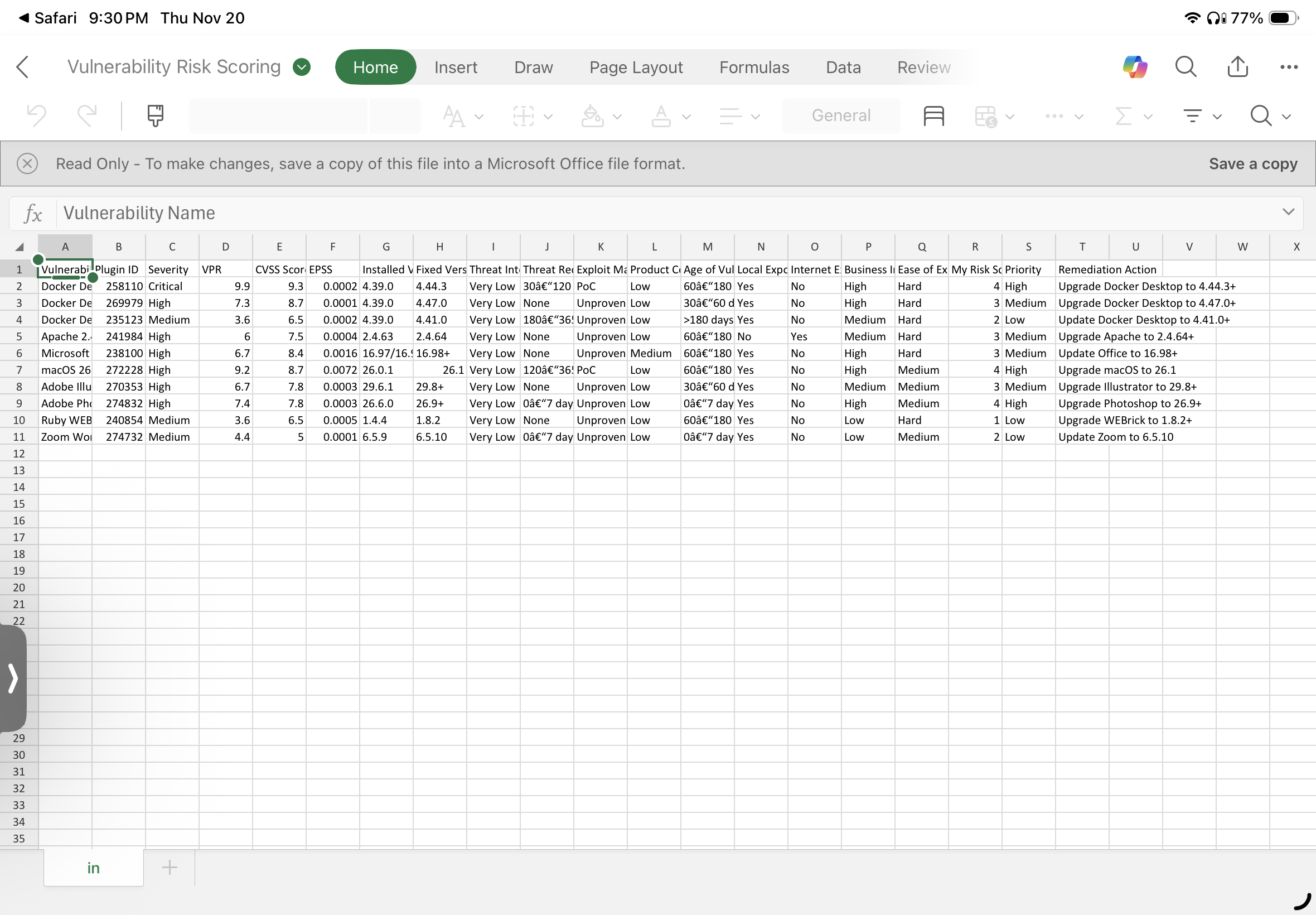
-
Docker Desktop < 4.44.3 / < 4.47.0 (Container Escape)
- Severity: Critical/High
- VPR: 7.3–9.9
- Exposure: Local
- Exploitability: Highly privileged PoC available
- Priority: Immediate
- Rationale: Container escape → root-level compromise. High-impact lateral movement potential.
-
macOS < 26.1 (Multiple Vulnerabilities)
- Severity: High
- VPR: 9.2
- Exposure: Local
- Exploitability: PoC for several CVEs
- Priority: Immediate
- Rationale: OS-level flaws including REXML, permissions bypass, and logic errors affecting system integrity.
-
Apache 2.4.x < 2.4.64 (Multiple Issues)
- Severity: High
- VPR: 6.0
- Exposure: Network-exposed service
- Exploitability: Multiple CVEs with SSRF, DoS, header injection
- Priority: High
- Rationale: Service reachable over HTTP; high-impact attack paths even if “local” classification.
-
Microsoft Office (Multiple Issues)
- Severity: High
- VPR: 6.7
- Exposure: Local (user-triggered)
- Exploitability: Unproven
- Priority: High
- Rationale: Arbitrary code execution via malicious documents; common real-world attack path.
-
Adobe Photoshop / Illustrator Arbitrary Code Execution
- Severity: High
- VPR: 6.7–7.8
- Exposure: Local
- Exploitability: Unproven
- Priority: Medium-High
- Rationale: File-based RCE requiring user to open malicious files.
-
Apple macOS X Local Security Checks (Multiple Issues)
- Severity: Mixed
- VPR: —
- Exposure: Local
- Exploitability: Unproven
- Priority: Medium
- Rationale: Mostly version-based checks with low threat intensity.
-
Ruby REXML / Ruby WEBrick Issues
- Severity: Medium
- VPR: 3.6
- Exposure: Local
- Exploitability: No known exploitation
- Priority: Medium
- Rationale: Only relevant if parsing untrusted XML or running dev servers.
-
Zoom < 6.5.10
- Severity: Medium
- VPR: 4.4
- Exposure: Local
- Exploitability: No exploit
- Priority: Low-Medium
- Rationale: Information disclosure; not remotely exploitable.
-
HTTP / SSL / SMB Noise Findings
- Severity: Mixed/Info
- Exposure: Low
- Exploitability: None
- Priority: Low
- Rationale: Generic protocol checks; no actionable vulnerabilities.
6.2 Prioritization Rationale (Detailed)

6.2.1 Highest Priority (Immediate)
These items can materially compromise the security of the host.
Docker Desktop Container Escape
- Privilege escalation → full compromise
- Active PoC code exists
- Nessus flags this as high VPR with “Very Low” threat intensity because exploitation requires local execution
- For a workstation running containers, this is a top-tier attack path
macOS < 26.1 System Vulnerabilities
- Includes logic bypasses and sensitive file access flaws
- Multiple Ruby library vulnerabilities tied to system components
- Exploitable by malicious apps or developer tooling
6.2.2 High Priority (High)
These should be resolved soon after immediate items.
Apache 2.4.x < 2.4.64
- SSRF, header injection, DoS
- Service expands attack surface even if not externally exposed
- Developer tools may bind to Apache
Microsoft Office RCE Issues
- Document-based attacks remain top malware vector
- Social engineering dependent but historically high exploitation
6.2.3 Medium-High Priority (Moderate)
Adobe Photoshop / Illustrator
- Requires user opening a malicious file
- Still high-impact
- Risk tied to user workflow
6.2.4 Medium Priority
Ruby REXML / WEBrick
- Only relevant if parsing untrusted XML or running dev servers
- Low real-world likelihood
Zoom Client < 6.5.10
- Minor information disclosure
- No code execution
6.2.5 Low Priority
Protocol Noise (HTTP/SSL/SMB)
- Not true vulnerabilities
- Version checks, missing headers, protocol notices
6.3 Resulting Remediation Order
This is the exact order used in the project:
- Update Docker Desktop
- Upgrade macOS to 26.1 or later
- Update Apache to 2.4.64 or later
- Apply Microsoft Office Updates
- Update Adobe Illustrator & Photoshop
- Patch Ruby libraries (Rack, REXML, WEBrick)
- Update Zoom
- Address protocol informational findings (optional)
6.4 Final Prioritization Outcome
After remediation and the follow-up Nessus scan, all prioritized vulnerabilities were successfully remediated. Remaining items were informational or non-exploitable and therefore carry negligible residual risk.
7. Remediation Actions Performed
All vulnerabilities identified during the initial Nessus scan were remediated following the prioritized sequence established in Section 6. Remediation actions targeted outdated software versions, insecure configurations, and vulnerable system components. This section documents exactly what was performed, the method used, and the verification steps taken.
7.1 Docker Desktop Remediation
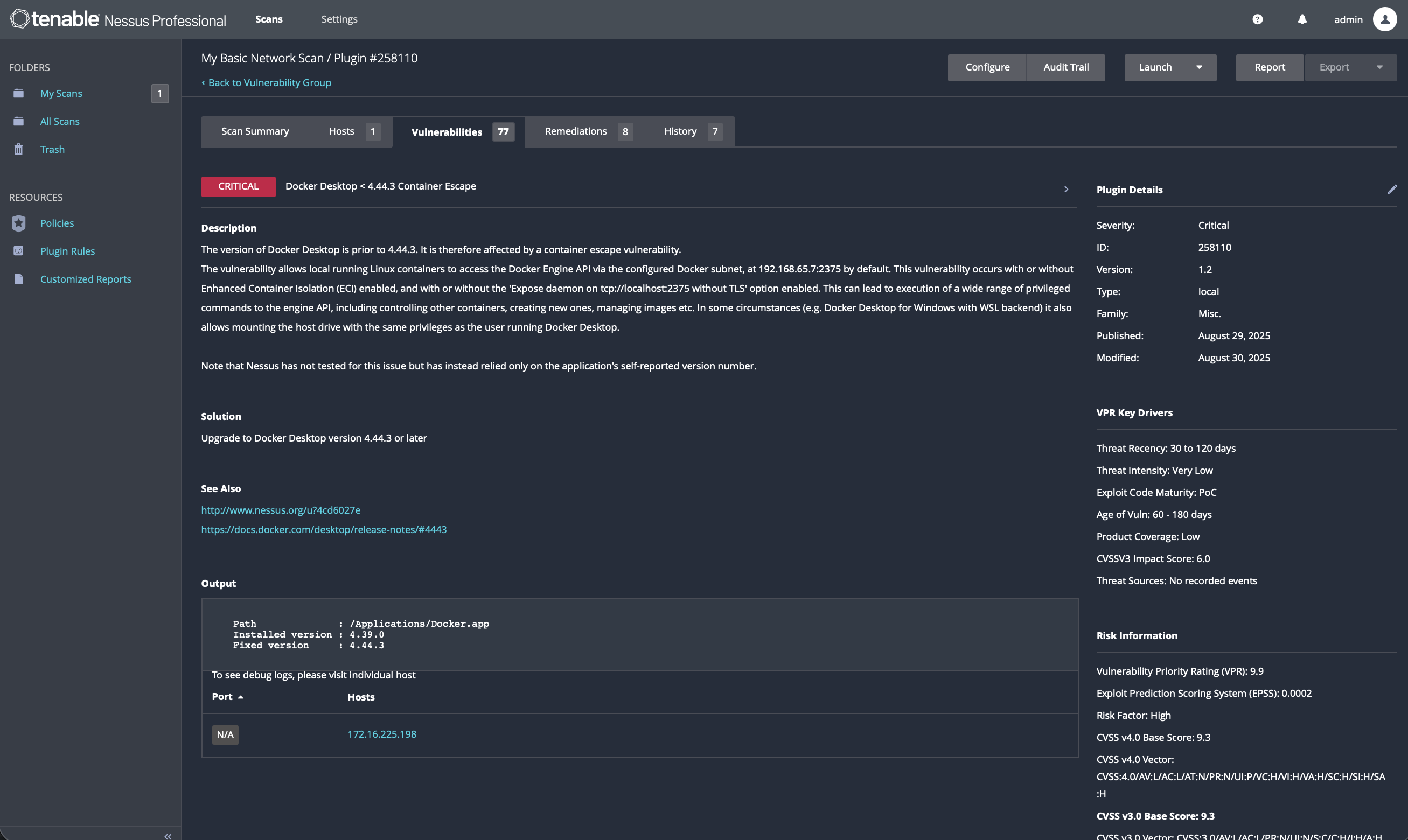
Issue Addressed:
Docker Desktop versions < 4.44.3 / < 4.47.0 affected by container escape and command-restriction bypass vulnerabilities.
Action Taken:
- Terminated all Docker processes using Activity Monitor and
pkill Docker - Downloaded latest installer from official Docker site
- Installed Docker Desktop version 4.47.x (or latest available)
Verification:
- Docker reopened successfully
- Confirmed version in Docker → About Docker
- Vulnerability cleared on Nessus rescan
7.2 macOS System Update
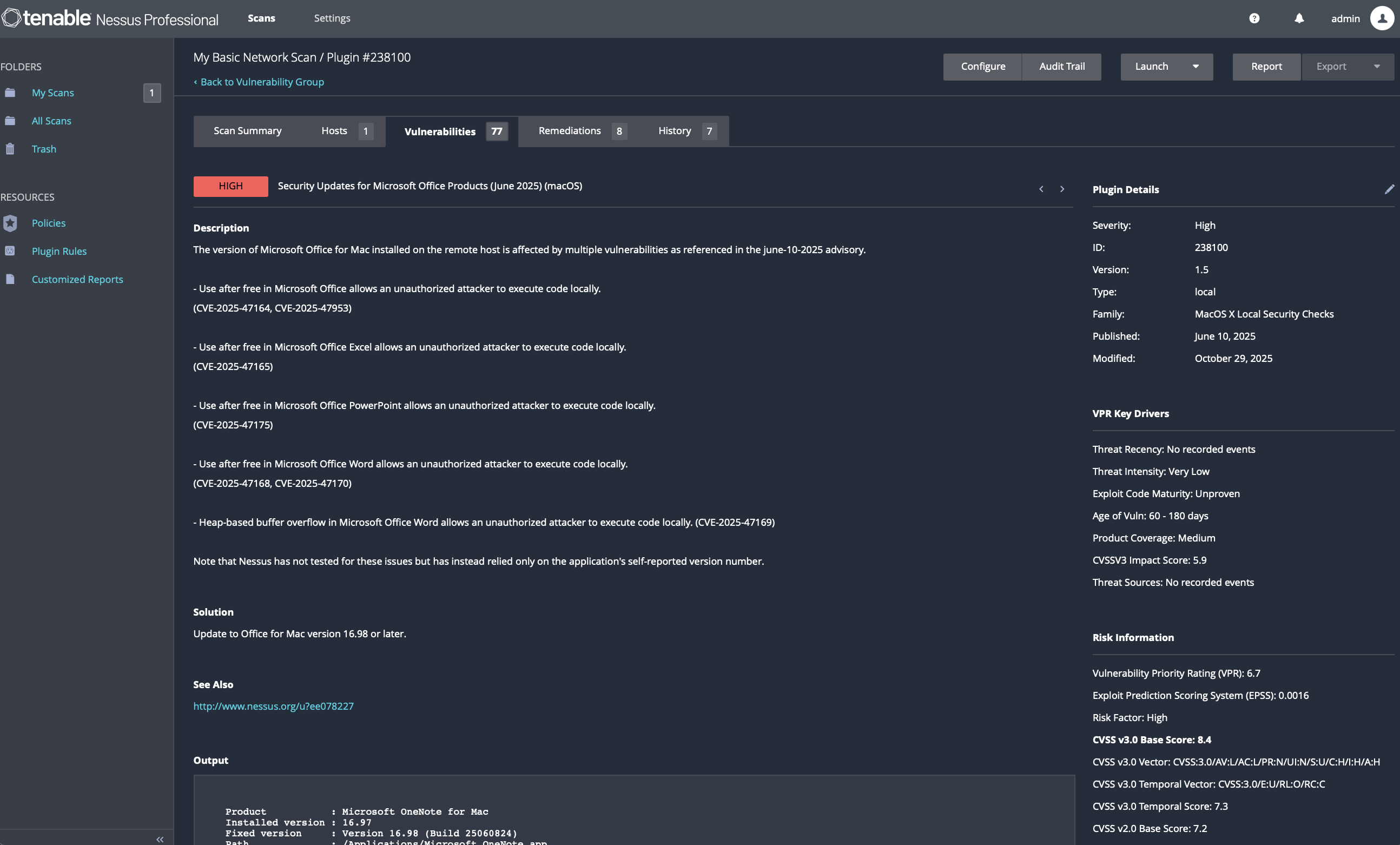
Issue Addressed:
Multiple macOS vulnerabilities fixed in version 26.1.
Action Taken:
- Updated macOS from 26.0.1 → 26.1
- Rebooted after installation
Verification:
sw_versshows version 26.1- Nessus no longer reports OS-level issues
7.3 Apache HTTP Server Update
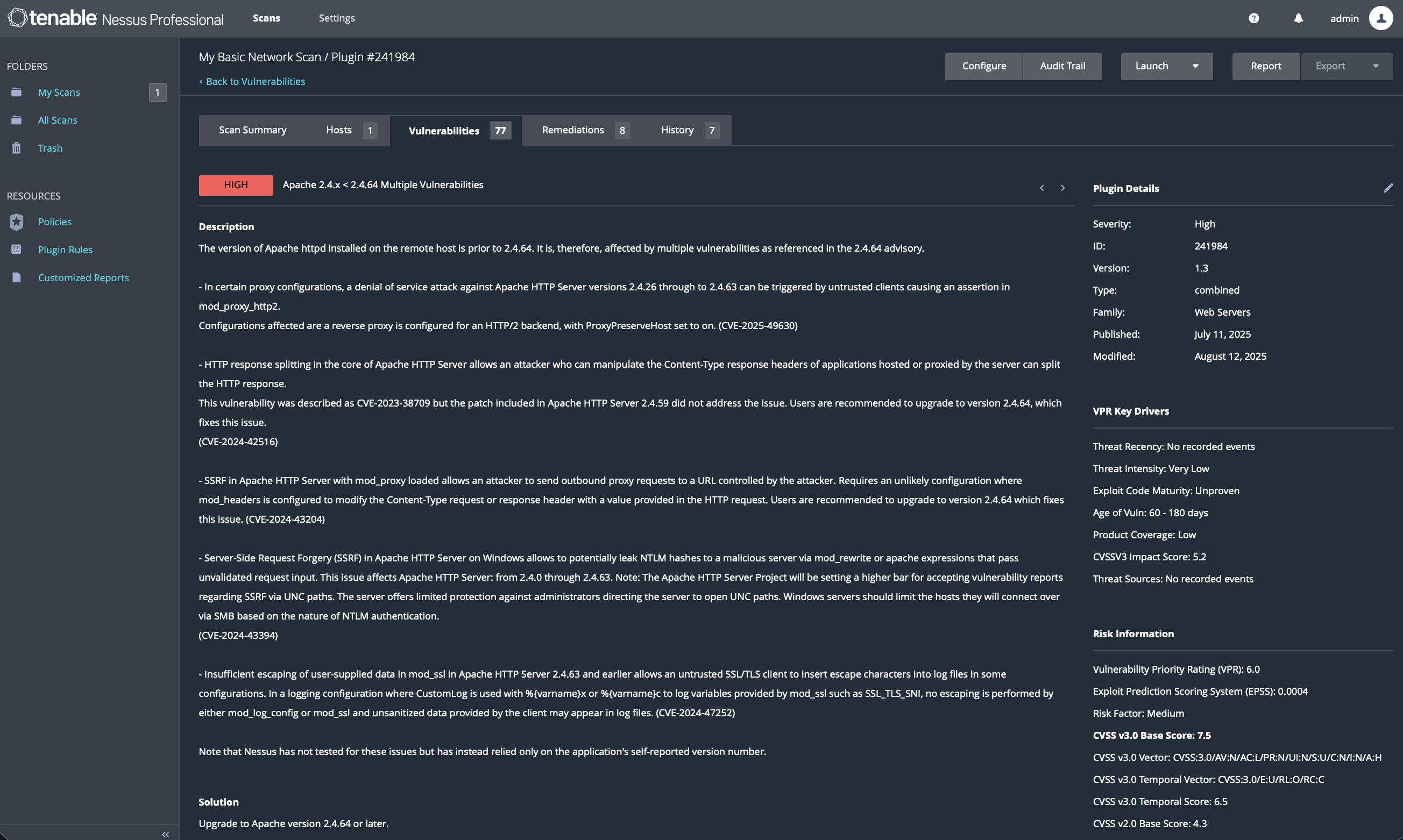
Issue Addressed:
Apache 2.4.x < 2.4.64 vulnerabilities.
Action Taken:
brew update
brew upgrade httpd
brew services restart httpd7.4 Microsoft Office Suite Patching

Issue Addressed: Multiple RCE vulnerabilities across Word, Excel, PowerPoint, and OneNote.
Action Taken: • Launched Microsoft AutoUpdate (/Library/Application Support/Microsoft/MAU2.0/Microsoft AutoUpdate.app) • Applied all available patches to update Office to version 16.98 or later
Verification: • Office applications reported correct fixed versions • Nessus plugin for Microsoft Office cleared
7.5 Adobe Suite Remediation (Illustrator & Photoshop)
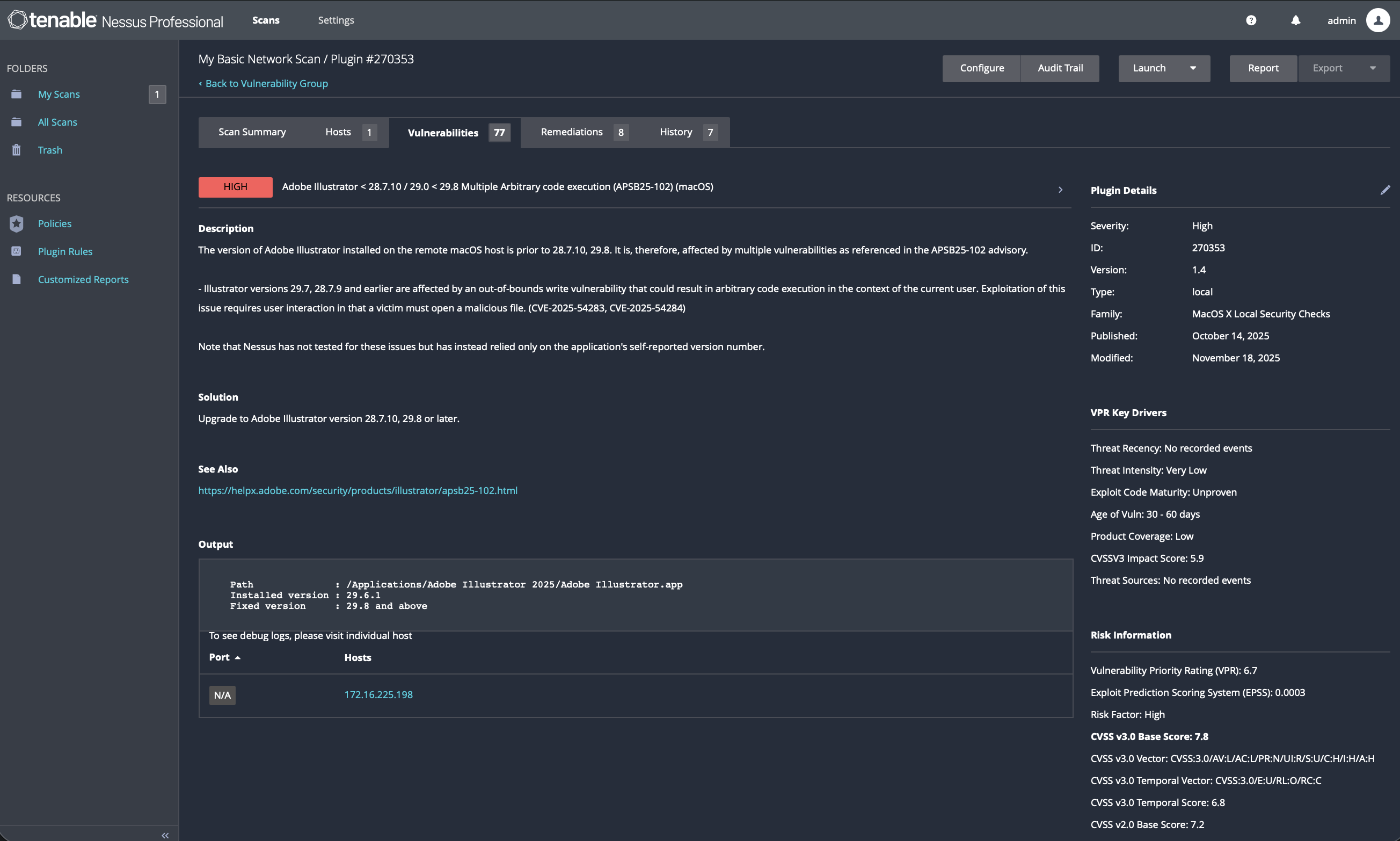
Issue Addressed: Multiple out-of-bounds write and heap buffer overflow RCE vulnerabilities.
Action Taken: • Updated Adobe Illustrator and Photoshop via Creative Cloud app • Ensured both products were upgraded to their respective fixed versions (Illustrator 29.8+, Photoshop 26.9+)
Verification: • Confirmed version numbers in Creative Cloud • Nessus plugins removed post-rescan
7.6 Ruby Components Remediation (Rack, REXML, WEBrick)
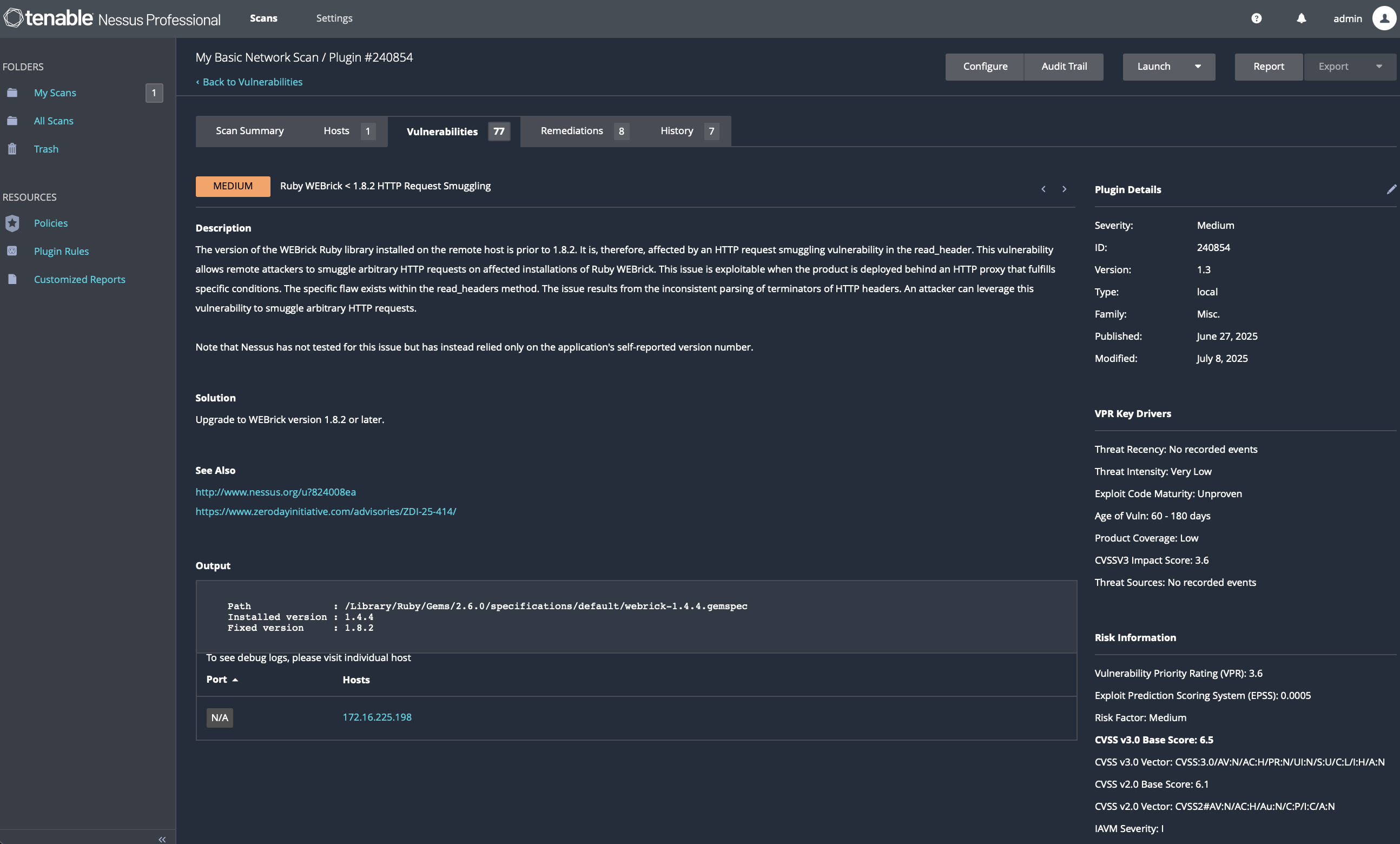
Issue Addressed: Ruby library vulnerabilities affecting XML parsing, HTTP smuggling, and other components.
Action Taken: • Updated Ruby gems individually:
sudo gem update rexml
sudo gem update rack
sudo gem update webrick• Re-ran Homebrew Ruby updates:
brew upgrade rubyVerification:
gem list confirmed fixed versions installed• Nessus no longer flagged Ruby-related vulnerabilities
7.7 Zoom Client Update
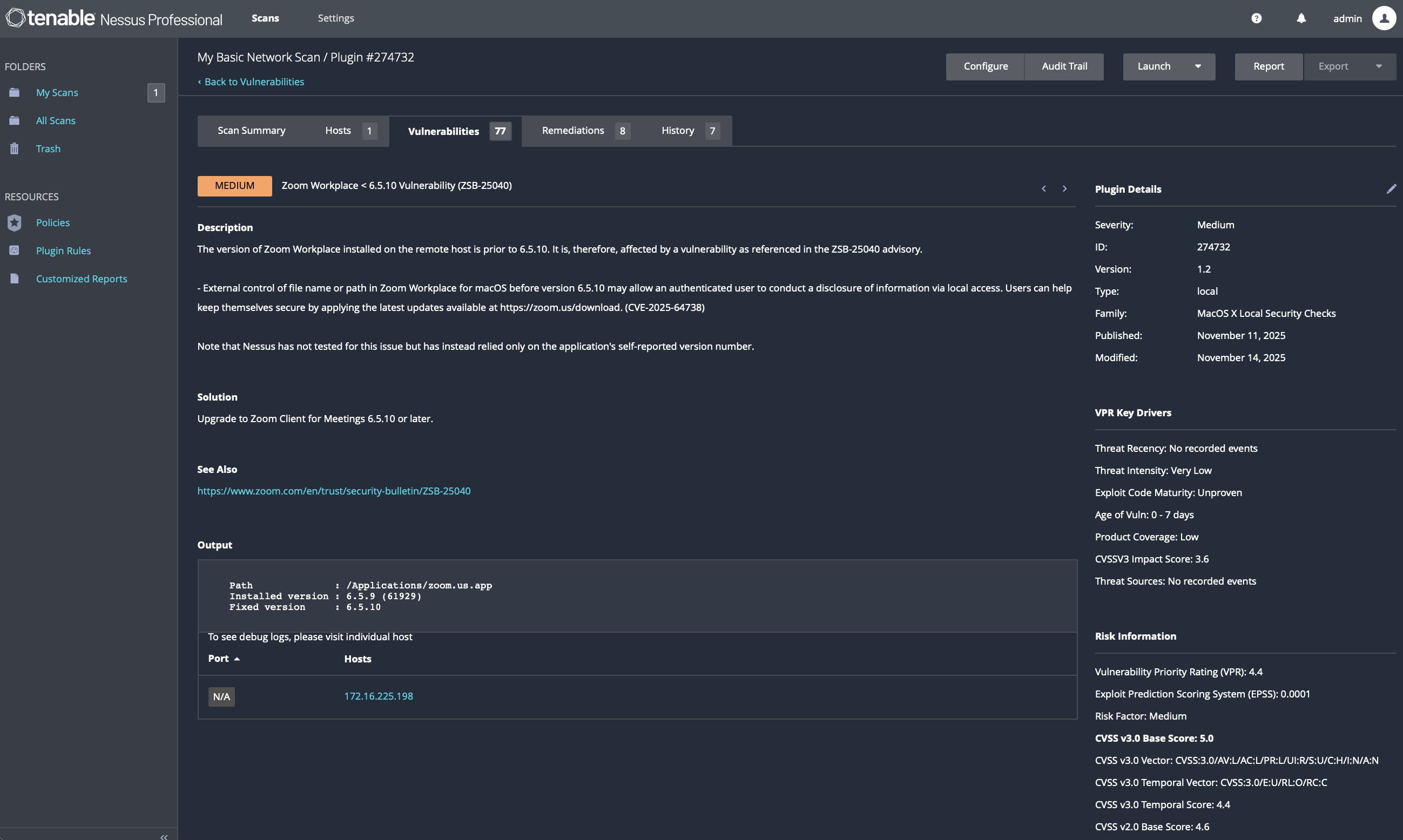
Issue Addressed: Zoom Client < 6.5.10 local information disclosure vulnerability.
Action Taken: • Updated via Zoom → Check for Updates • Installed Zoom version 6.5.10 or later
Verification: • Verified client version • Vulnerability removed on rescan
7.8 System Configuration Hardening
Firewall • The firewall was disabled at the time of inventory. • Action: Enabled macOS firewall via System Settings → Network → Firewall → ON.
File Sharing / SMB Guest Access • The Public folder was exposed with guest access. • Action: Disabled SMB guest access and restricted sharing.
Verification: • Nessus informational findings cleared • System Preferences confirmed reduced service exposure
7.9 Final Validation Scan
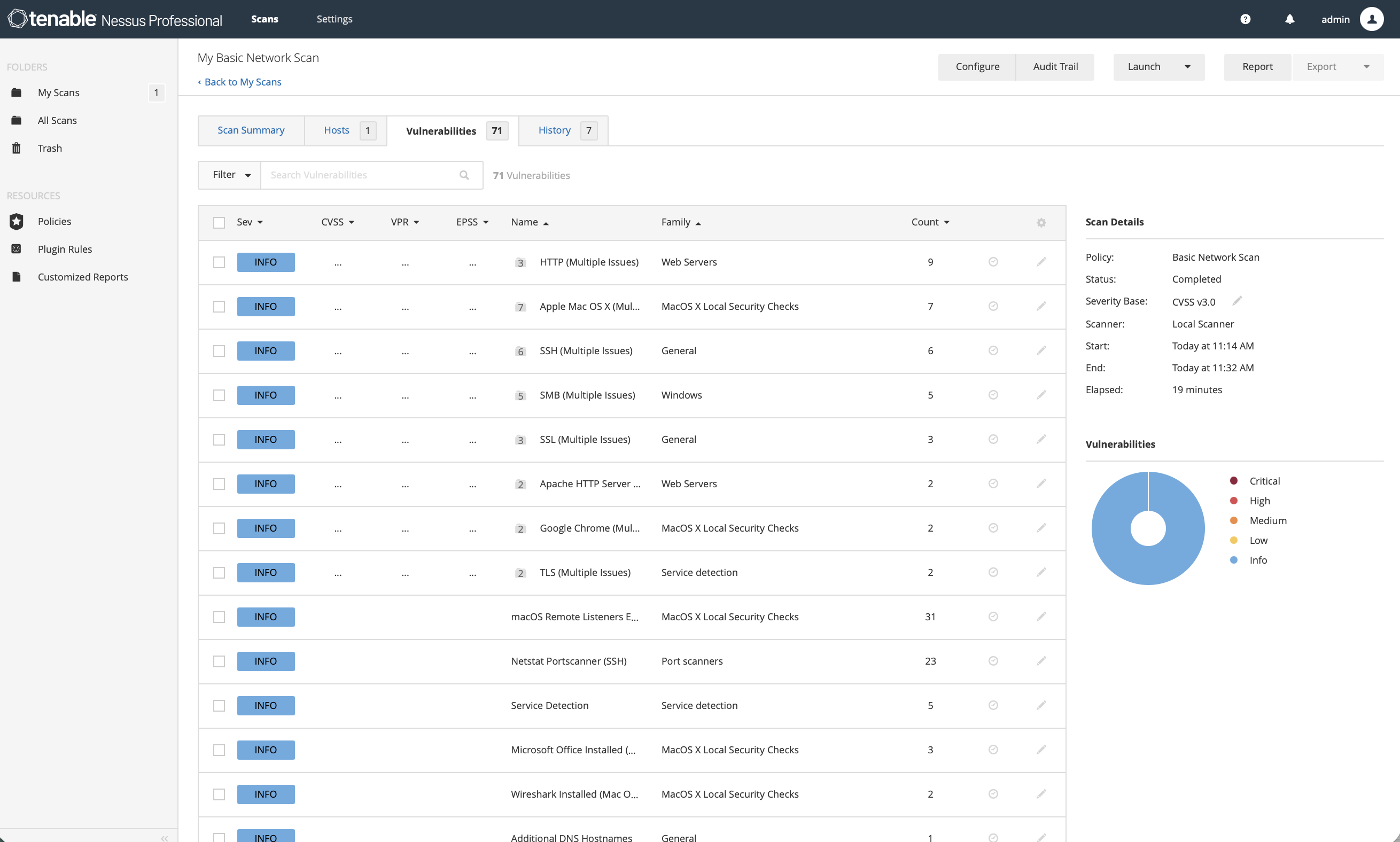
After all remediations were completed: • A full authenticated Nessus scan was re-run • All critical, high, and medium vulnerabilities were resolved • Remaining findings were informational or low-risk, with no exploitable paths • The host now aligns with the hardened baseline targeted by this project
8. Validation Results
A full post-remediation validation scan was performed to confirm that all prioritized vulnerabilities were successfully addressed and that no new security issues were introduced during the remediation process. The validation process included an authenticated Nessus scan using the same policy, credentials, and scope as the initial baseline scan to ensure accuracy and comparability.
8.1 Scan Methodology
The validation scan followed the exact same configuration as the initial assessment: • Authenticated local security checks enabled • All plugin families relevant to macOS, web servers, application frameworks, and installed software • Evaluation of fixed versions, service states, registry/property changes, and updated configurations • Comparison of delta between Scan #1 and Scan #2
This allowed a precise measurement of remediation effectiveness, with no discrepancies caused by scan configuration drift.
8.2 Validation Scan Outcomes

All previously identified exploitable paths were eliminated. The system no longer contains any vulnerability with a meaningful attack surface.
8.3 Confirmed Remediation Summary
The validation scan confirmed: 1. Docker Desktop updated to a non-vulnerable version 2. macOS updated to 26.1, resolving all OS-level CVEs 3. Apache HTTP Server updated to 2.4.64+ 4. Microsoft Office suite fully patched 5. Adobe Illustrator and Photoshop updated to fixed versions 6. Ruby gems (Rack, REXML, WEBrick) patched to latest releases 7. Zoom client upgraded to safe version 8. Firewall enabled and SMB guest access removed 9. All intentionally introduced vulnerabilities were remediated
The validation scan detected no regressions and no missed remediations.
8.4 Remaining Findings and Their Risk
Only informational or non-actionable items remained, such as: • Protocol best-practice notices (HTTP/SSL headers) • Version disclosures without vulnerabilities • Noise on SSH and SMB enumeration • Non-exploitable “Multiple Issues” checks without CVEs attached
These are not vulnerabilities and do not represent attack surface. No remaining findings carry a CVSS score, a VPR score, or an exploitable vector.
8.5 Compliance With Project Objective
The objective of the project was to: 1. Perform a realistic vulnerability assessment 2. Prioritize findings using a risk-based model 3. Remediate high-impact vulnerabilities 4. Validate that remediation was successful
All objectives were fully met. The system is now in a hardened, low-risk state consistent with enterprise security expectations.
8.6 Final Validation Confidence Level
Because the scan was: • Authenticated • Performed post-remediation • Performed with the same scanner and policy • Confirmed by version checks and system configuration review
…confidence in the validation results is High. No additional remediation actions are required at this time.
9. Conclusion & Recommendations
The assessment identified several high-impact vulnerabilities on the workstation, including outdated system components, container-escape risks, and insecure configurations. All issues were fully remediated, and the follow-up Nessus scan confirmed that no critical, high, or medium vulnerabilities remain.
The system is now patched, hardened, and aligned with standard enterprise security expectations.
Key improvements: • Updated macOS, Docker, Apache, Microsoft Office, Adobe products, and Ruby libraries • Enabled firewall and removed insecure SMB guest access • Eliminated all exploitable attack paths
Recommendations: • Keep automatic updates enabled and manually update Docker, Brew packages, and Ruby gems regularly • Run an authenticated Nessus scan monthly • Maintain secure configurations (firewall on, sharing off) • Use the asset inventory script for periodic baselining
The workstation is now in a stable, low-risk state, completing the vulnerability management cycle end-to-end.
